23 Nov What is a risk vs threat vs vulnerability?
What’s the difference among risks, threats, and vulnerabilities? What about hazards? And how does a risk assessment differ from a threat assessment or a vulnerability assessment? These are questions that confuse even seasoned security professionals. In this post we’ll walk you through these definitions. Arguably the most important thing to remember is that risk comprises a few elements.
Threat
The U.S. Department of Homeland Security defines a threat as “a natural or man-made occurrence, individual, entity, or action that has or indicates the potential to harm life, information, operations, the environment, and/or property.” A threat is usually an external source of risk to an organization, and many security professionals also consider threats to be always man-made, intentional, and with malice.

In some cases, a threat can be an internal source of risk, such as insider threat. According to the National Insider Threat Task Force (NITTF) “an insider is any person with authorized access to an organization’s resources to include personnel, facilities, information, equipment, networks, or systems.” The NITTF defines insider threat as “the risk an insider will use their authorized access, wittingly or unwittingly, to do harm to their organization.” Other threats include terrorist attacks, active shooters, economic criminals, non-terrorist workplace violence, subversives, and petty criminals.
For the purpose of calculating risk, threat likelihood is estimated based on the intent and capability of the adversary, and can be measured by frequency or probability of the threat. Threats and their likelihood can be measured qualitatively or quantitatively. A qualitative measure of threat can be phrased as “high”, “medium”, or “low”, as in “The threat of a terrorist attack against this facility is low.” A quantitative example: If a successful burglary against a strip mall has consistently occurred once per week over the course of several months, we can assess that there’s a 1 in 7 probability of a burglary occurring at that strip mall any given day of the week. Or put another way, there’s a burglary threat at that strip mall, and there’s about a 14% (1 divided by 7 — the number of days in a week) chance of that threat occurring on a Monday, or a Tuesday, or a Wednesday, etc.. Of course, with enough data on the specific days of the week the burglaries occur and also against which specific stores, we might be able to increase the accuracy and fidelity of our quantitative threat assessment.
Often, there’s little to nothing organizations and even governments can do to eliminate some threats. There are exceptions, such as with some crime (e.g., the burglary example above). But usually mitigation measures are best focused on reducing vulnerabilities and consequences.
Vulnerability

A vulnerability is the physical feature or operational attribute that renders an entity open to exploitation or susceptible to a given threat or hazard. In calculating the risk of an intentional threat, a common measure of vulnerability is the likelihood that an attack is successful, given that it is attempted. Consider a cat stalking a mouse. The cat is the threat, and the mouse is vulnerable — the latter’s vulnerabilities include its small size (a physical feature) and inadequate defensive (operational) attribute that can mitigate against the cat’s attack.
As previously mentioned, vulnerabilities — unlike most threats — is one of the one of the only components of risk that can be changed — for good or bad. For example, in the cat and mouse example above, the mouse can’t modify the threat the cat poses to it. However, the mouse can choose when and where to roam, thereby reducing its vulnerability to the cat. Similarly, a you can’t change the threats to yourself when you travel domestically or internationally; you don’t have the power to make terrorists, muggers, pickpockets and infectious diseases suddenly disappear. However, you can reduce or eliminate your vulnerability to threats in a vacation spot or business travel location by leaving, cancelling your trip, or taking other measures when advised by your country’s embassy or security professionals. The threat hasn’t changed, but you have changed your vulnerability.
Consequence
 Similar to our ability to affect our vulnerabilities, we have can change the consequences of of threats and hazards — for good or bad. For example, companies can mitigate against various adverse events by conducting business continuity planning, to include pandemic planning. And families and individuals can ensure they have the proper insurance coverage and other planning to mitigate against various threats and hazards. While nothing can be done to prevent a hurricane, companies, home owners, and home renters can reduce the consequences of hurricanes by ensuring they have flood insurance, developing plans to communicate with employees, and developing evacuation plans (to include “go-bags”).
Similar to our ability to affect our vulnerabilities, we have can change the consequences of of threats and hazards — for good or bad. For example, companies can mitigate against various adverse events by conducting business continuity planning, to include pandemic planning. And families and individuals can ensure they have the proper insurance coverage and other planning to mitigate against various threats and hazards. While nothing can be done to prevent a hurricane, companies, home owners, and home renters can reduce the consequences of hurricanes by ensuring they have flood insurance, developing plans to communicate with employees, and developing evacuation plans (to include “go-bags”).Hazard
Threats and hazards are often conflated, but sometimes it’s beneficial to differentiate between the two. While threats are always intentional (putting aside unwitting insider threats), and with malice, hazards can be either natural or man-made and are unintentional or without malice. The most common hazards are naturally occurring events. These natural hazards vary by region and can vary even within a state/province. In the U.S. mid-Atlantic region (New York, New Jersey, Pennsylvania, Maryland, Delaware and Washington, DC.), hurricanes and winter storms are the most significant natural hazards. Hazards also include utility (water, power, and gas) disruptions and accidental chemical spills. Remember that hazards are unintentional or without malice. Chemical spills are often man-made, but unintentional or without malice. Like threats, hazards are also measured by their likelihood, or probability.
Risk
While there are many definitions of risk, at a basic level it is the potential for an unwanted outcome resulting from an incident, event, or occurrence, as determined by its likelihood and the associated consequences. Let’s break down this definition:
- “incident, event, or occurrence” means a threat or hazard.
- “determined by its likelihood” — Remember that one measure of threat is its likelihood, or its probability. Sometimes likelihood is considered a function of threat and vulnerability.
- “and the associated consequences” — the final element of many definitions of risk.
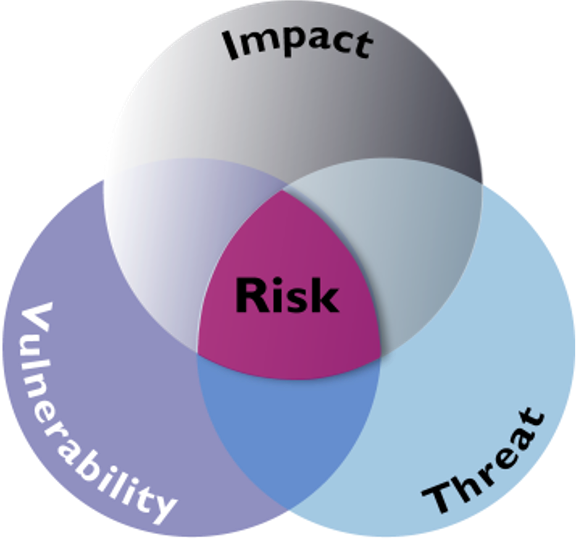
Hence, one definition of risk is threat x vulnerability x consequence. Remember that sometimes the term “impact” is used in lieu of “consequence” — so you might also see risk = threat x vulnerability x impact.
You might also see matrices that depict risk as function of probability and impact. But remember the synonyms. Probability is another way to say likelihood, or threat. If the cat is mouse-friendly, there’s little to no probability the cat will attack the mouse; the cat is not a threat. The other axis represents impact, which is synonymous with consequence. What about vulnerability? Well, the downside of a two-dimensional matrix is that it can represent only two variables (this is one reason why matrices such as the one shown to the right are falling out of favor with risk managers). In this case, some people might include vulnerability in the measure of impact. So if our asset isn’t vulnerable, there will be no impact. Or if our mouse were to gain Mighty Mouse powers, it would not be vulnerable to the cat, and therefor there would be little to no impact, or consequence, of the cat’s attack.
another way to say likelihood, or threat. If the cat is mouse-friendly, there’s little to no probability the cat will attack the mouse; the cat is not a threat. The other axis represents impact, which is synonymous with consequence. What about vulnerability? Well, the downside of a two-dimensional matrix is that it can represent only two variables (this is one reason why matrices such as the one shown to the right are falling out of favor with risk managers). In this case, some people might include vulnerability in the measure of impact. So if our asset isn’t vulnerable, there will be no impact. Or if our mouse were to gain Mighty Mouse powers, it would not be vulnerable to the cat, and therefor there would be little to no impact, or consequence, of the cat’s attack.
You might also see some risk methodologies that depict risk as the relationship among threat, vulnerability and ass ets. That’s not a favorite for us here at Blue Glacier, as we find “asset” to be redundant for a couple of reasons. First, risk is assessed for a specific asset, event, plan, activity etc, which arguably makes placing asset in the equation redundant. Secondly, the asset is “covered” by vulnerability in the equation. After all, you’re assessing the vulnerability of the asset, event, plan, activity. To use our cat and mouse analogy, that would be similar to identifying and assessing the cat as the threat (correct), then assessing the vulnerability of the mouse (makes sense), and assessing the mouse as the asset (hmmm. We just assessed the mouse during the vulnerability assessment).
ets. That’s not a favorite for us here at Blue Glacier, as we find “asset” to be redundant for a couple of reasons. First, risk is assessed for a specific asset, event, plan, activity etc, which arguably makes placing asset in the equation redundant. Secondly, the asset is “covered” by vulnerability in the equation. After all, you’re assessing the vulnerability of the asset, event, plan, activity. To use our cat and mouse analogy, that would be similar to identifying and assessing the cat as the threat (correct), then assessing the vulnerability of the mouse (makes sense), and assessing the mouse as the asset (hmmm. We just assessed the mouse during the vulnerability assessment).
There are many methodologies for risk, but you might have noticed some consistencies among the few we’ve briefly discussed. Consequence, or impact, is was a factor in two of the methodologies. Threat was part of all three, even if one of them used “probability” (synonymous with likelihood, or threat) instead of “threat”. Again, the most important thing to remember is that a few variables make up risk. Governments, organizations and families would make far better informed decisions if they understand and remember this concept. If you’re seeking a risk assessment, try to pick a security risk professional who, regardless of the methodology he or she chooses, understands the relationships among these concepts.
No Comments